Source: The East African (2014)
Author: Caleb Septoff
Perhaps one of the greatest scientific achievements in human history is the invention of the internet, which landmarked the beginning of the digital age in the modern era. Its uses span multiple fields and in large part is responsible for the high levels of rapid globalization we have become accustomed to today. Although it has improved humanity in many facets, it has also led to the increase in the susceptibility of nations’ and individuals to cyber-attacks. The internet has evolved over the last decade with the inception of social media and cyber currency, but with this evolution comes a new wave of terrorism in the form of cyber-attacks, propaganda, hacking, and online recruitment. The threat has grown substantially – enough for even university institutions, namely New York University (NYU), to offer cyber security majors and courses solely to deter these types of attacks.
Before venturing into the subject of digital terrorism, it is important to explore something less widely known to the average internet user; this being the deep web and dark net. The internet is composed of two main points of access; the surface web and the dark web. The surface web is most common to everyday users and comprises mainly of search engines, like Google and Bing, and the information found is unrestricted. Comparatively, the deep web differs mainly in size, estimated at four to five hundred times bigger than the surface web, accounting for 90% of the internet. In comparison to the surface web, the wealth of information stored on the deep web is gigantic. Most of the deep web is restricted by applications, which grant access to databases or password protected sites. Anything from social media, such as Facebook or Instagram, to online banking are considered part of the deep web. In addition to its size, the dark web differs in its accessibility. Despite popular beliefs, the deep web and dark net are not synonymous. Rather, the dark net exists hidden below the surface web. The dark net is almost entirely unregulated and is even harder to access than the deep web. To date, the dark net hosts an unknown number of websites, but the content ranges from people sending messages who wish to maintain anonymity to underground drug dealing, sex trafficking, weapons dealing, and the focus of this article, terrorists and extremists’ sites.
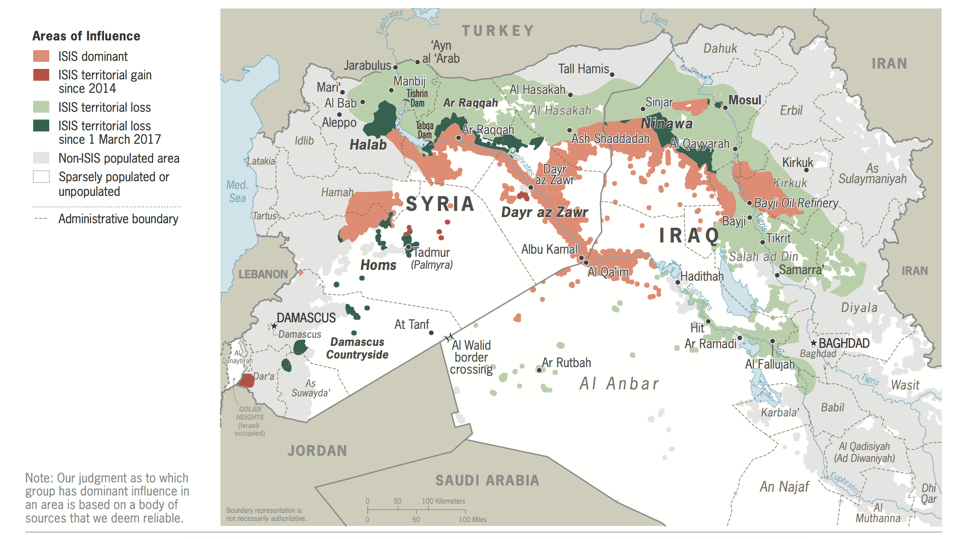
The Islamic State of Iraq and the Levant (ISIL) or Daesh, was the first terrorist organization to truly maximize their outreach using the internet. When Abu Bakar al-Baghdadi declared the caliphate, a wave of propaganda and recruitment media took social media by storm. While destructive, authorities and the companies themselves were able to mitigate much of the content since it took place on the more accessible surface web. However, the organization consistently found new ways to respond to authorities’ crackdowns. First, they began attracting people through social media and other corners of the surface web and then slowly moved them towards more difficult protected places like domains and chat rooms on the dark net. In addition, the use of messaging applications that offered heavy encryption, like Telegram, were core ways for them to communicate. The use of these cyber tools aided in attracting over 20,000 foreign fighters from more than 10 different countries to flock to Syria to fight on ISIL’s behalf, and even more followers aided the organization from remote positions around the globe. In early 2018, New York Times’ reporter, Rukimini Callimachi, released a podcast by the name of “Caliphate.” The podcast goes into detail about one Canadian man’s experience of being recruited through multiple steps, starting on social media and eventually moving into private chat rooms. Callimachi’s reporting highlights how effective ISIL’s extensive reach was, not only technologically, but by simply creating effective connections with people, especially the youth.
Thus far, terrorists’ groups have not been able to do much more than the defacement of webpages and execution of minor cases of hacking. For example, a series of attacks in 2015, all claiming ties to Daesh, were executed in various countries. Most notably, a self-titled group called Cyber Caliphate managed to hack Malaysia Airlines’ main website, deface the French TV5 broadcast station, and hack the US military Central Command’s YouTube and Twitter accounts. Technology is continuously growing and it gets more sophisticated every year. As greater attention turns to digital recruitment and terrorism, these “small” attacks will grow larger in scope and harm. The possibility of cutting electric to hospitals or inciting mass riots through the spread of false media is very real and dangerous. The need to find adequate responses to the rising dangers of cyber terrorism is crucial to the future of counter terrorism. Perhaps most conspicuously, the important question becomes how to best be proactive in thwarting attacks and rather than simply being reactive.
The international community has a plethora of different third-party watch dogs when it comes to war and terrorism, whether they come in the form of global entities like the United Nations (UN) or International Non-Profit Organizations (INGO). In addition, a multitude of international treaties and agreements exist to set standards for war and outline what is not acceptable. The Geneva Convention, one of the most important and widely known, is comprised of four treaties and three protocols that establish standards for humanitarian rights and treatment during times of war. Yet, something these organizations don’t cover adequately is how to respond to cyber warfare and digital terrorism. One of the greatest challenges in dealing with these online threats is attribution, or ascribing blame to those who have committed the crime and proving it. According to a RAND Corporation video on the subject, they identify three main types of attribution: political (dealing with diplomatic knowledge and political actors’ objectives), technical (IP addresses, log file analysis, etc.), and clandestine (classified information and political insights).
Categorizing makes it easier to decide how to interpret the crime and, thus, how to assign punishment. However, it is not simple to prove digital crimes without access to data that, for the most part, is private, anonymous and not easily tracked. Citizens’ right to privacy and the level of privacy that is entitled has become a topic of high contention in the debate for higher cyber security. Although these are difficult issues to deal with, the international community needs to step up and begin to take action before cyber warfare reaches a level with much higher stakes. Like the UN, there needs to be a large international organization that can specialize in cyber security and cyber terrorism. It would require the nonexistence of any political affiliation to be effective and act on behalf of any country that requires its services to increase its credibility. Perhaps, most important, would be its role in providing international laws on cyber warfare and attacks to clearly and concisely build a foundation or framework for security agencies to work from. It would also be responsible for developing the mechanisms for freedom of expression and privacy; although this would most likely fall to the specific countries rather than the independent watch dog organization.
Social media platforms have done relatively well at combing through their users and content to locate possible terrorist activities, but this is not enough. Further action needs to be taken regarding regulation. Systems need to be devised to adequately monitor both the surface web content and the deep and dark web to locate, deter and respond to these threats before they can implement harm to critical infrastructures, governments, businesses, and even the psyches of viewers. Creating measures to regulate data and prevent data mining for terrorist activities is crucial to preventing the attacks in the future. There is no easy answer to the rising threat of cyber terrorism and warfare, but it’s imperative that solutions and international cooperation begins sooner than later.