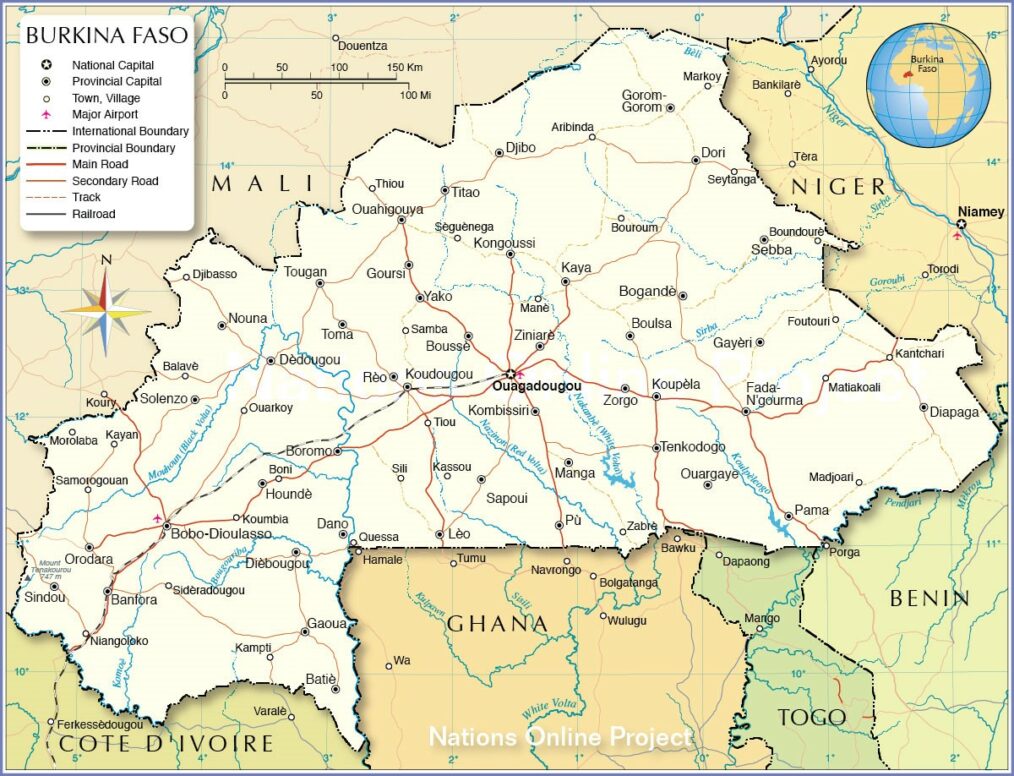
Figure 1 Retrieved from Nationsonline.org Link
Rampant political instability in Burkina Faso, stemming from the overthrow of dictator Blaise Compaoré, has resulted in a rapidly expanding crisis for counter-terror operations in the tri-border region between Mali, Burkina Faso, and Niger. Ongoing conflicts across the region are complicated by local issues that reach back hundreds of years, such as ethnic and tribal divisions, combined with modern global terror networks that are exploiting the instability. Efforts to solve these issues have global significance; the United States has actively trained regional security and military forces to better equip them to combat terrorists, while France has conducted ongoing military operations in Burkina Faso, Niger, and Mali.
Since 2016, there have been 200 terror attacks in Burkina Faso, with at least 263 confirmed deaths stemming from these attacks. This is astounding considering that prior to the removal of Compaoré, Burkina Faso had never experienced a terror attack in its recorded history. While some of these attacks have been attributed to former elite special forces of the military of Burkina Faso from Compaoré’s regime, several terror networks operate in the area. Al Qaeda in the Islamic Maghreb (AQIM) and the Islamic State in the Greater Sahara (ISGS) remain the largest regional representatives of global terror operating in the region and have conducted ongoing attacks across multiple countries, capitalizing on weakened governments and ethnic and tribal conflicts. Local militias have been known to engage the global terror networks in armed conflict on occasion as the militaries and other security forces appear to be ineffective or incapable of conducting military operations against them.
The Burkinabé military, which was trained by French and U.S. special forces, has contributed to further instability. Counterterror operations conducted by the Burkinabé military have resulted in accusations of false arrests, extrajudicial killings, and other abuses- further eroding trust between local communities and the weak government. Both ISGS and AQIM will likely be able to capitalize on these strained relationships to increase recruiting capabilities as their affiliates globally have done in the past. Terror groups have begun to cement their long-term presence in Burkina Faso, operating at least partially in the open and driving the shutdown of many schools and hospitals. The closing of these establishments represents the failures of local government, and highlights the government’s inability to conduct successful counterterror operations. The school closures also decrease opportunities for local youth, increasing the likelihood that they will ultimately turn to extremism.
ISGS was created by Abu Walid al Sahrawi, who previously had allegiance to al Qaeda. ISGS still recruits heavily from al Qaeda ranks, but saw a drop in activity after recent French military operations killed several of its high-ranking members. Like so many terror groups in the past, ISGS operates most successfully in areas with weakened government institutions with weak border regions. Until further stabilization is secured in the region, counterterror operations will be unsuccessful in the long-term.
France has recognized the need to develop stability in the tri-border region as critical to African security. French foreign minister Jean-Yves Le Drian pledged €34 million to programs that will increase stability in the areas between Burkina Faso, Mali, and Niger. However, this funding will likely be insufficient to solve the vast underlying issues that are contributing to the destabilization. The U.S., who is already devoting significant funds to the region by way of military training and military equipment, must increase funding and develop solutions that will legitimize the governments of Burkina Faso, Mali, and Niger. Corruption, which is an issue observed in each of these countries, must be addressed to ensure further legitimacy as well as to ensure that the funds being devoted to stabilization go to appropriate channels on the ground.
John Patrick Wilson is a Research Fellow with Rise to Peace and a Law Enforcement Professional.